Today I had my system infected with a trojan. I don’t even remember when it was the last time to have one… The worst part of it – I didn’t get it by visiting dubious sites (pr0n, warez), but from a news site (http://news.com). Most likely the malware was masquerading as an ad and exploited some unpatched hole in Adobe Flash (caveat!) as the site is full of Flash advertisements and had problems in the past, too.
I was browsing the news and suddenly the browser disappeared (crashed). I restarted it thanking Adobe and thinking nothing more of it. Soon after that, problems appeared.
The first red flag was an elevated prompt from Windows 7, asking for permission to run ‘SoftwareUpdate.exe’. Since I was not installing anything, I canceled it. Yet the prompt came again, and again, and again. From the dialog’s details, the program was "c:\Users\alinc\AppData\Local\temp\SoftwareUpdates.exe", so I renamed the executable to *.exe_ extension, and canceled the prompt again. This time I got error messages that updates can’t be installed, so I set up to investigate who was displaying it. To my surprise, I could not launch TaskManger (taskmgr.exe) nor SysInternal’s ProcessExplorer (procexp.exe). As soon as the programs were started, they were closed automatically... It was clear now I was infected.
I logged off, and switched users, logging in with a different local Administrator account. Problems occurred here as well, I still could not launch ProcExp. Soon I started to get tons of error messages “A Write command during the test failed to complete”, culminating with a “System error, hard disk failure detected”. All the icons on desktop disappeared leaving only one “Smart_Hdd” shortcut.

I opened a command prompt and stated to see problem here as well - folders and files disappeared from ‘dir’ commands. I renamed procexp.exe to something else (alin.exe) and this way I was able to launch it without being closed anymore. You can see in one look Process Explorer highlighted in gray 2 suspect programs (C:\ProgramData\rmIhrYfwFjUdy.exe and C:\ProgramData\QFUDzzwTiL1aQy.exe): they had weird names, were launched from ProgramData, had no Description or CompanyName.
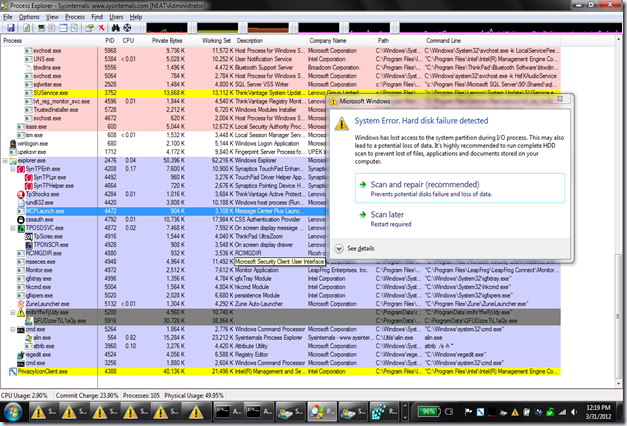
Even more worrying, rmIhrYfwFjUdy.exe had launched a recursive “attrib.exe /s +h \*.*” (not shown, I killed it immediately)– this was hiding all the files and folders on my computer! I believe all these was a scamming scheme to convince me into buying some “cleanup program” that would fix the “hard drive failures” “detected” and reported in the previous messages.
I tried to stop/kill the malicious programs by pressing Delete, but those were protecting each other – as soon as one was killed, the other one was immediately starting it up again. The solution is to right click them, and use “Suspend” command. Suspend both, then you’ll be able to kill them without coming back. Now I could move the binaries out of the way for my collection and investigate further.
I run another Sysinternal/Microsoft tool, Autoruns. This indicated rmIhrYfwFjUdy.exe was launched at logon time via a registry value written under HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. I deleted that as well.
I updated Microsoft Security Essentials to the latest definitions, and I started a scan. With latest definitions, it flagged as malware two of the binaries. QFUDzzwTiL1aQy was recognized as Win32/Bumat!rts, and SoftwareUpdate was recognized as Win32/Tibs!IT. The 3rd program was not recognized, so I used the Microsoft’s Virus Submission Sample Page to submit rmIhrYfwFjUdy.exe for further analysis.
The trojan left more traces on my computer:
- The "Smart HDD" shortcut on desktop pointing to QFUDzzwTiL1aQy.
- A “Smart HDD” program group with 2 entries, one masquerading as an “Uninstall” program, but pointing to the same malware.
- Most folders and files were hidden. I had to run recursive ‘attrib –h’ of my own to reset attributes.
- The StartMenu and Taskbar settings were all changed. All the icons in start menus were hidden, the taskbar was set with Vista-like settings (program buttons with texts, no grouping, system tray showing all icons, etc). I had to go to Properties and explicitly set or reset all to defaults.

- All icons under “Administrative Tools” were deleted. In fact, the whole “C:\ProgramData\Microsoft\Windows\Start Menu” folder was cleaned of all files.

- The “C:\Users\All Users” folder is also gone. There may be other effects I haven’t found yet…
Basically I’ve lost all the shortcuts/icons of all installed programs, but I’m still pleased I caught it in time before it caused more damage - the situation could have been much worse…
In any case, this was one more win for Sysinternals tools.


15 comments:
My prayers were answered - the deleted shortcuts were not really deleted, just moved somewhere else on the disk (probably so they can be restored quickly if I'd have bought the scammer's fake "disk repair/virus cleanup" program).
The Start Menus shortcuts were all moved to "C:\Users\Alinc\AppData\Local\Temp\smtmp\1" - to restore them I copied them back to "C:\ProgramData\Microsoft\Windows\Start Menu".
And the shortcuts that were on desktop were now in "C:\Users\Alinc\AppData\Local\Temp\smtmp\4", again easy to restore.
I had the exact same thing happen to me on the same day March 31 2012 at just before 6pm est.
I was watching a Weird Al music video playlist on youtube when the SoftwareUpdate.exe popup showed and although I clicked No I was still infected.
I used Malwarebytes antimalware and a bleeping computer tool called unhide to repair the damage.
The ironic thing is I had just ordered Malwarebytes Pro that may have prevented the entire thing a few days ago and it just hadn't arrived yet. I got it from here: http://www.newegg.com/Product/Product.aspx?Item=N82E16832562001
I also used a $8.00 off coupon that was sent to me so it and the 8gb usb together was only $15 with free shipping.
Anyway, the unhide cleaned up most of the issues. Besides that I had to go into personalize desktop and start menu setting and restore my settings.
I found some program called Unhide on this link http://deletemalware.blogspot.com/2011/11/remove-system-fix-uninstall-guide.html
to restore all of my shortcuts as the C drive icons were visible again.
I have the same rmIhrYfwFjUdy.exe file in my ProgramData folder that is auto starting when I boot my system. How did you delete it? I can't figure out how to delete or disable, when I try it gives the message that "The action can't be completed because the file is open in FRGD"
Hi Alin,
I contracted the same malware on Friday, and I've been Googling for solutions since then. Just found your blog, followed the instructions and now my PC is clean again.
Just wanted to say thank you.
Sean
Same thing happened to me while browsing yahoo news with Firefox. Tried to bring up Task Manager to see if Firefox was still running and was unable to launch it which keyed me right away. Fortunately it seems running XP, it wasn't nearly so destructive. Used autoruns to find "rmIhrYfwFjUdy.exe" and deleted it the launch. Thanks.
The same happened to me. Your report was very helpful, thanks! In my case the virus was setting the attribute +s (system file) in addition to the +h.
Fun fact: the virus is activated on March 30, International Backup Day.
I just had the same thing, and this was the only result google brought back. Thank you for knowing what you are doing - I got my system secured again in minutes.
Alin, my computer got infected by the same trojan this afternoon. Thanks to your blog post, I was able track down and delete the malicious files. I'm not a tech guy by any means, but I am decent at following instructions. I was never able to find the stash of shortcuts you mentions in your last comment and the trojan seemed to either delete or hide all of my pictures, video and documents. I did a back-up a few months ago so if everything did get deleted, it only means I lost a few months of pictures and not my entire library of photos and video. Any idea if these items got deleted or maybe their still hidden?
Alin Constantin thanks for the tip, my computer was also infected by the same virus (trojan) Your topic was very important to me! Health and Peace
MSSE definitions have been updated to detect these threats. As I suspected, one of the binaries was a scareware trojan, Trojan:Win32/FakeSysdef. It looks like I stopped it in time, it didn't got the chance to alter the registry.
There was another malware associated, Exploit:Java/CVE-2010-0840.QF, so this could have been the attack vector and not Flash. Damn Java, too.
@Drew: With ProcessExplorer, right click one by one the 2 malware programs, choose Suspend. When both are suspended, you can then kill the processes without respawning again (use Delete=KillProcess, or any other kill tool, e.g. TaskManager). One you have killed the processes you should be able to delete the exe files on disk.
Or follow the method described here - rename the exe binaries to something else, then reboot. If newer variants of the malware don't monitor the disk changes to rename the file back, after reboot the malware will not run and you'll be able to delete it.
http://deletemalware.blogspot.com/2011/09/how-to-remove-data-recovery-uninstall.html
@Dan: I bet the files are on your computer too (so they can be "magically" restored if you fall for the scam and buy their scareware). If you trust that unhide.exe utility Drew found you can give it a try, but personally I'd be scared to run it without sources.
I found where the malware stashed the files in my case by looking for *.lnk files (those are the shortcuts).
E.g. after resetting the files attributes with "attrib /s -h C:\*.*", in command prompt I run "dir /s /b C:\*.lnk" - this showed me most of the files were now in that %temp%\smtmp folder, so I just copied them back in the right place.
If you're missing documents and pictures you can also search for *.jpg, or search based on filenames (e.g. my Canon camera produces files like IMG_1234.jpg, so I'd search for IMG_*.* in case the malware changed the extensions). I'd also search for very large files with WinExplorer in case the malware archived them (zip/rar/etc archive). I hope you'll get your files back.
Got hit with this yesterday, as well, as did a friend. I wonder what updated yesterday to spawn this on the world?
Thanks for your blog, I got my machine mostly back to normal within 90 minutes.
Alin, my wife found all of the files late last night; they were hidden (phew!). On another note, Microsoft Security Essentials found and deleted about 16 different Exploit:Java/CVE files after the infection. Thanks again for your help.
Very grateful for your post. Hit this over the weekend too. Thank you!
This is a post from 2012 - it has been temporarily taken down by BlogSpot for a claimed DCMA violation. Really I want to see where is the copyright violation in screenshots captured on my machine. So here is the article republished again...
Post a Comment